Yes, smart AC systems can be hacked. These devices, connected via the Internet of Things (IoT), often rely on outdated security protocols, weak default passwords, and unencrypted communication methods, making them vulnerable to cyberattacks. Hackers can exploit these flaws to take control of devices, disrupt operations, or even recruit them into botnets for larger attacks.
Key vulnerabilities include:
- Unsecured Communication Protocols: Many systems use MQTT or HTTP without encryption, allowing attackers to intercept or manipulate data.
- Weak Passwords and Firmware: Factory-set credentials and outdated firmware create easy entry points for attackers.
- Network Configuration Risks: Poorly segmented networks can expose smart AC systems to broader cyber threats.
Real-world examples highlight these risks:
- In 2022, researchers found Electra Smart AC controllers allowed anonymous logins via an open MQTT server.
- In 2026, Mitsubishi Electric disclosed a critical flaw (CVE-2025-3699) that allowed unauthorized control over 27 AC models.
- Unencrypted firmware updates and RF signals have been exploited to manipulate devices or spread malware.
To secure your smart AC system:
- Use strong, unique passwords and enable multi-factor authentication.
- Ensure firmware updates are cryptographically signed and applied regularly.
- Isolate smart devices on a separate network or behind firewalls.
- Avoid exposing systems directly to the internet; use VPNs for remote access.
While these systems offer convenience, their security risks demand proactive measures to protect personal data and prevent larger-scale disruptions.
Keep your HVAC system from being HACKED!
sbb-itb-b5c10b1
Security Vulnerabilities in Smart AC Systems
Smart AC System Security Vulnerabilities and CVE Scores
Smart AC systems face weaknesses in three key areas: communication methods, authentication and firmware, and network configuration. These vulnerabilities create opportunities for the exploits described in the following section.
Unsecured Communication Protocols
Many smart AC systems rely on communication protocols that lack proper security measures. For instance, MQTT (Message Queuing Telemetry Transport) and radio frequency signals often transmit data without encryption or authentication, making it easy for attackers to intercept or manipulate commands.
In June 2023, researchers Lev Aronsky and Idan Strovinsky from Aleph Security uncovered a significant flaw in Electra Smart AC controllers. The system’s MQTT server allowed anyone with access to a device’s MAC address to remotely control countless units. Aronsky highlighted the issue:
"There was an MQTT server, open to anyone over the Internet, that allowed anonymous logins with permission to control any Electra Smart air conditioner connected to the network".
Radio frequency commands used by utility companies to manage AC loads during high-demand periods are also susceptible. Attackers with basic equipment can hijack these signals. Bitdefender researchers discovered that the Bosch BCC100 thermostat’s Wi-Fi chip forwarded unauthenticated traffic from TCP port 8899 directly to its main microcontroller, making it unable to distinguish between legitimate and malicious commands. Weak password practices only make matters worse.
Weak Default Passwords and Outdated Firmware
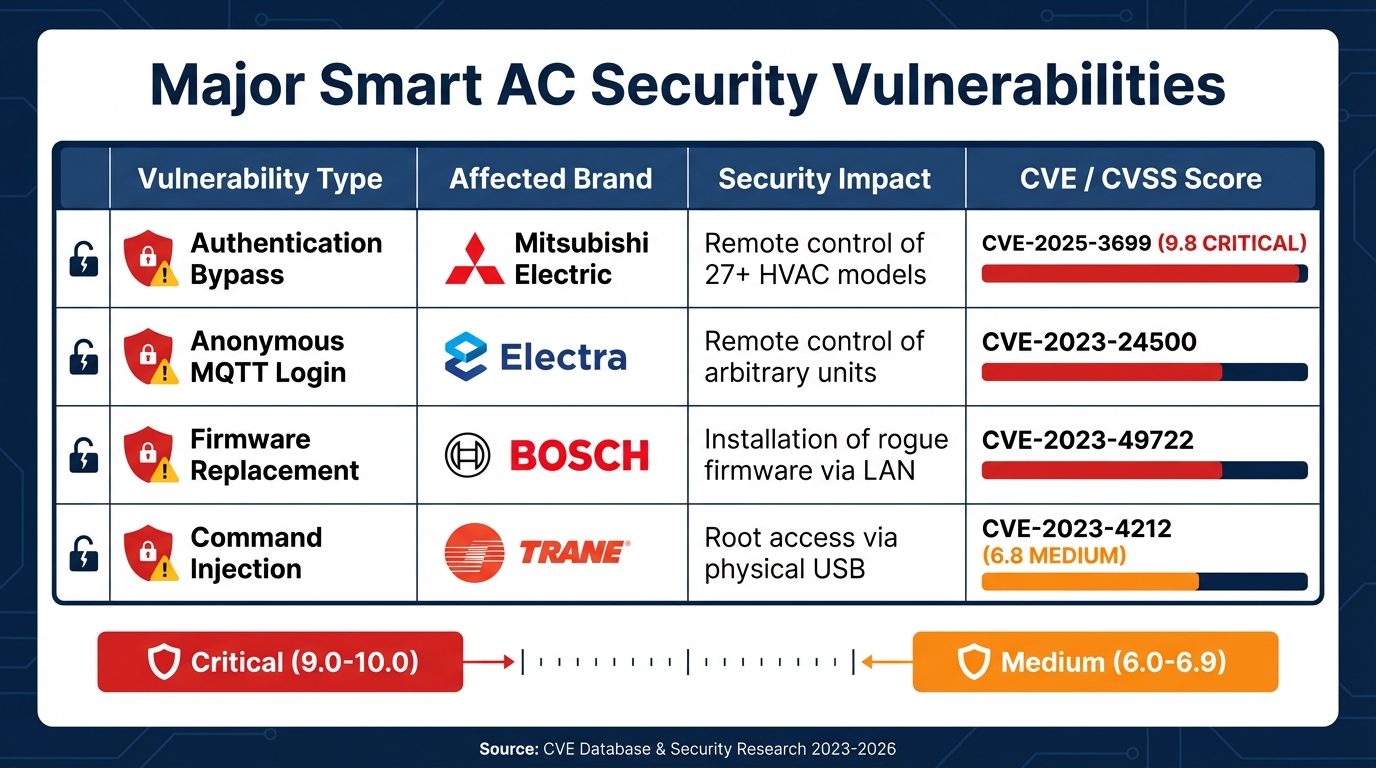
Factory-set credentials and neglected firmware updates provide easy entry points for attackers. In February 2026, Mitsubishi Electric disclosed CVE-2025-3699, a critical flaw (CVSS 9.8) identified by researcher Mihály Csonka. This "Missing Authentication for Critical Function" issue affected 27 AC models, including the AE-200 and EW-50 series, and allowed attackers to bypass authentication and gain full control over building HVAC systems.
Firmware updates themselves can introduce vulnerabilities. Aleph Security researchers examining Electra Smart controllers (Revision 008) found that updates were downloaded via unencrypted HTTP connections and verified only with an MD5 checksum instead of a more secure digital signature. This made it possible for attackers to impersonate the update server and push malicious firmware.
Some issues persist for years. In August 2023, researcher Houlton McGuinn disclosed CVE-2023-4212, a command injection flaw affecting Trane XL824, XL850, and XL1050 smart thermostats. This vulnerability, present since 2015, allowed anyone with physical access to execute arbitrary code as the root user by using a specially crafted filename on a USB drive during software upgrades.
Network Configuration Risks
Poor network segmentation often turns smart AC systems into entry points for larger attacks. When HVAC devices share a network with computers or business systems, a compromised thermostat can act as a gateway to more sensitive targets. Mitsubishi Electric emphasized this risk in their CVE-2025-3699 disclosure:
"The vulnerability poses the greatest risk in improperly configured environments where air conditioning systems are directly accessible from the internet without VPN protection".
Many systems are set up with direct internet access instead of being secured behind firewalls or VPNs. This issue was evident in the Electra case, where controllers could be accessed from anywhere online. Legacy hardware complicates matters further – older components often lack the processing power needed for modern authentication techniques and cannot be upgraded without full replacement.
| Vulnerability Type | Example Brand | Impact | CVE / CVSS Score |
|---|---|---|---|
| Authentication Bypass | Mitsubishi Electric | Remote control of 27+ HVAC models | CVE-2025-3699 (9.8) |
| Anonymous MQTT Login | Electra | Remote control of arbitrary units | CVE-2023-24500 |
| Firmware Replacement | Bosch | Installation of rogue firmware via LAN | CVE-2023-49722 |
| Command Injection | Trane | Root access via physical USB | CVE-2023-4212 (6.8) |
Professional HVAC services can help address these vulnerabilities, which is essential to counter the hacker techniques discussed in the next section.
How Hackers Exploit Smart AC Systems
Hackers have found ways to exploit vulnerabilities in smart AC systems, enabling them to take control or even disrupt entire networks. These attacks range from direct remote commands to more complex strategies that leverage compromised devices for broader malicious purposes.
Remote Access Exploits
One common tactic involves targeting unsecured MQTT servers, which are often used to manage smart AC units. In June 2023, researchers Lev Aronsky and Idan Strovinsky from Aleph Security highlighted this issue with Electra Smart AC controllers. They discovered that the manufacturer’s MQTT server allowed anonymous logins, making it accessible from anywhere on the internet.
Another example of remote access vulnerabilities includes the CVE-2025-3699 disclosure from February 2026. This flaw affected certain Mitsubishi Electric AC models, enabling attackers to gain unauthorized control without requiring any user action. These weaknesses open the door to more advanced interference methods.
Man-in-the-Middle and Malware Attacks
Unencrypted communication channels present another major risk. For instance, Electra Smart controllers used unencrypted HTTP connections to download firmware updates, without verifying digital signatures. This allowed attackers to perform Man-in-the-Middle attacks, redirecting devices to malicious servers and forcing them to install compromised firmware containing arbitrary code.
Radio frequency (RF) attacks are another avenue of exploitation. At the February 2016 Kaspersky Security Analyst Summit, researchers Vasilios Hioureas and Thomas Kinsey demonstrated how utility-controlled AC shut-off devices could be hijacked. These systems relied on unencrypted RF signals, making them vulnerable to replay attacks. By recording "on" or "off" commands and broadcasting them with stronger signals, attackers could easily manipulate multiple units. Kinsey explained the potential scale of such attacks:
"Anyone with $50 can generate a signal that can trump a repeater [to take out a few air conditioners]; and anyone with $150 can generate that through an [amplifier] and presumably take out a whole neighborhood".
In September 2017, researchers at Ben-Gurion University of the Negev introduced the HVACKer proof-of-concept. They demonstrated how compromised internet-connected HVAC systems could communicate with malware on air-gapped computers by adjusting room temperature. The malware then used the computer’s thermal sensors to decode these fluctuations into binary data at a rate of 40 bits per second.
These communication flaws not only allow attackers to interfere with individual systems but also enable them to integrate compromised devices into larger attack networks.
Botnet Recruitment of IoT Devices
Once compromised, smart AC systems can be turned into bots for Distributed Denial of Service (DDoS) attacks. For example, the ability to push malicious firmware updates, as shown in the Electra research, makes it possible for attackers to convert these devices into tools for scanning networks or launching DDoS attacks.
Security experts have also warned about the potential for synchronized attacks. By turning thousands of AC units on or off simultaneously, hackers could create massive power surges or imbalances, potentially tripping circuit breakers and causing widespread blackouts in municipal power grids.
How to Secure Smart AC Systems
Protecting your smart AC system from potential threats requires proactive measures. The steps below address the vulnerabilities and risks previously highlighted, offering practical ways to safeguard your devices.
Strong Authentication and Encryption
Start by changing default passwords to strong, unique ones. Many devices come with weak factory passwords that hackers can easily exploit. Adding multi-factor authentication (MFA) provides an extra layer of protection against unauthorized logins.
Ensure your system uses end-to-end encryption with modern protocols like TLS to secure communication between the AC unit, mobile app, and manufacturer servers. Disable anonymous access on MQTT brokers and configure the system to use secure ports, like port 8883, instead of unencrypted options like port 1883. Brendan O’Toole, Vice President of Sensi Product Platform at Copeland, highlights the importance of trusted encryption practices:
"Contractors can ease customer concerns by relaying that when it comes to data and personal information, smart thermostats leverage trusted industry standards and proven encryption and security techniques to ensure customer data is safe".
Additionally, make sure firmware updates are cryptographically signed by the manufacturer. This ensures attackers can’t install malicious updates. Avoid systems that rely on outdated algorithms like RC4, DES, or Triple DES, which are vulnerable after processing large amounts of data.
Keeping firmware secure and up to date is just as crucial as strong authentication.
Regular Firmware and Software Updates
Enable automatic updates for your system, ensuring they are cryptographically signed to prevent tampering. These updates often include fixes for known vulnerabilities. For example, Mitsubishi Electric released firmware updates in June 2022 (Version 7.98 or later) to address critical flaws like CVE-2022-24296, which allowed remote attackers to tamper with data. Systems that missed these updates remained at risk for attacks, including "Sweet32" and other cryptographic issues.
Replace outdated units that no longer receive updates. Some older HVAC systems, with control chips dating back to 1995, lack the hardware to support modern security protocols. Rina Basholli, Information Security Lead at Kode Labs, underscores the importance of timely updates:
"Regularly updating the software installed on the smart HVAC systems, which often include security patches that address security concerns, whether new or existing".
To further reduce risks, consider isolating your HVAC systems on a separate network.
Network Segmentation for HVAC Systems
Separate your smart AC system from your main network to limit damage if the device is compromised. For homeowners, this can be as simple as using a dedicated guest Wi-Fi network for IoT devices.
Businesses should take additional precautions by placing HVAC control systems behind firewalls and isolating them from the primary business network. If remote access is required, use a Virtual Private Network (VPN) instead of exposing the system directly to the internet. The Cybersecurity and Infrastructure Security Agency (CISA) advises:
"Locate control system networks and remote devices behind firewalls and isolate them from the business network".
For extra security, hide the HVAC network’s SSID and limit access to trusted devices. These steps can significantly reduce the chances of a breach.
Conclusion
Smart AC systems offer the dual benefits of convenience and energy efficiency, but they also come with notable cybersecurity risks. Weak default passwords and unencrypted communication protocols are just a few vulnerabilities that attackers can exploit to gain unauthorized access, manipulate settings, or even turn these devices into botnet recruits. Addressing these risks requires proactive security measures.
Adopting strong credentials, enabling multi-factor authentication, performing regular updates, and isolating devices on separate networks are essential steps. Yet, while 72% of smart home owners express concerns about device security, only 13% take the time to review manufacturers’ data privacy policies. This disconnect between awareness and action highlights the need for expert intervention.
To better protect your investment, working with the best HVAC services ensures your system is secure from installation through maintenance. These experts can implement advanced security measures such as network segmentation, cryptographically signed firmware updates, and regular audits to address vulnerabilities before they become a problem. As Rina Basholli, Information Security Lead at Kode Labs, emphasizes:
"User awareness is critical in maintaining a secure environment".
If you’re in the Chicagoland area, Eco Temp HVAC provides services to keep your smart AC system both efficient and secure. With certifications like the Mitsubishi Diamond Elite Contractor designation and 24/7 availability in Chicago, St. Charles, Bartlett, Lemont, Downers Grove, and Palatine, their team of certified technicians is ready to help you implement these best practices. Don’t wait – take action now to protect your home or business from potential security breaches.
FAQs
How can I tell if my smart AC has been hacked?
If your smart AC starts acting up, it could be more than a technical glitch. Here are some warning signs to watch for:
- Erratic temperature changes: If your AC suddenly cranks up the heat or cools down without you adjusting it, this could be a red flag.
- Unusual network activity: Keep an eye on your router or app for spikes in data usage linked to your AC. This might point to unauthorized access.
- Strange noises from connected devices: Odd sounds, like beeping or unexpected fan activity, could indicate tampering.
These behaviors might signal a security breach. It’s important to stay alert and regularly check your system for anything out of the ordinary.
What’s the safest way to set up remote access to my smart AC?
To ensure your smart AC’s remote access is secure, start by creating strong, unique passwords. Also, make sure your Wi-Fi network is encrypted – this is a crucial step in keeping your connection safe. Regularly update your device’s firmware to address security vulnerabilities, and if the option is available, enable two-factor authentication for an added layer of protection. For even more security, consider using a VPN when accessing your system remotely. These steps can significantly lower the chances of someone gaining unauthorized access to your smart AC.
Should I put my smart AC on a separate Wi‑Fi network?
Yes, connecting your smart AC to a separate Wi-Fi network is a good idea. Smart devices, including AC systems, can sometimes have outdated software or security gaps that make them targets for hackers. By isolating them from your primary network, you add an extra layer of protection for your sensitive data and other connected devices. To boost security even more, make sure to use strong, unique passwords and regularly update the device’s firmware.











